[MUSIC PLAYING] Hello, I'm Laura Rogers. And welcome to my session, Building Approval Processes and Power Apps. So before we get started, I'll go ahead and just tell you a little bit about myself. I live in Birmingham, Alabama. My company that I've founded is called IW Mentor. It's online training for SharePoint, Power Apps, Power Automate, and Teams. And you can find me on Twitter @wonderlaura and @IWMentor.
So first of all, let's talk a little bit about what this session is about. Here's our agenda. We'll talk about an introduction to the session in the concepts. And then I have this method that I'm going to be teaching you about building an entire approval process inside of a Power App.
So I'm going to talk to you about why you would want to do that and why I came up with this method. And then I'm going to get into the details. We'll talk about the lists involved and the structure of the Power App, how the logic works and the formulas inside of the Power App. And we even have a flow involved as part of this process, so I'll talk to you about what that entails. And then we'll finalize it, and I'll do a demo and show you how it all works.
So first of all, here's the concepts. So you have approval forms in your company. You probably have hundreds of them. They might be in different stages of how modern they are. You might still have people filling out pieces of paper and walking around and handing them to people at their desks. You might have PDFs that people print out. But you're probably have a lot of approval processes.
So you have things like travel requests, new employee forms, onboarding, check requests, and you can probably think of many of them in your company.
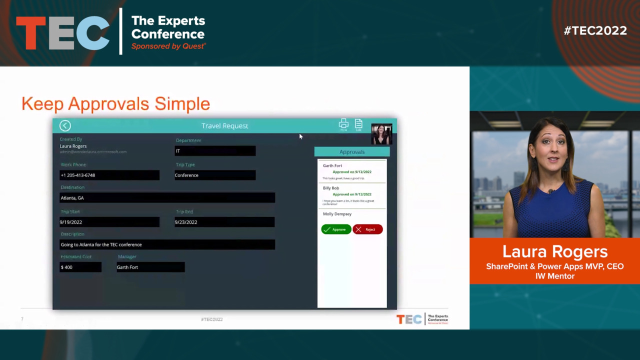
So my concept that I'm going to teach you today is what I like to do in Keep Approval Simple. Instead of having the approvers have a lot of different things that they have to look at and different links they have to click on and having the data living in different locations within Microsoft 365, this is a screenshot of my concept of having a form that someone fills out and having a very simple approval panel down the right so that when the approvers, when it's their turn to do something, it's very obvious and simple as to what they have to do.
They look at the form, and they click Approve or Reject. And then they're going to be presented with the ability to enter comments. And it goes from approver to approver. You can have as many as you like. And the form just keeps going down the side of the screen. So this is what I'm going to be talking to you about, why I'm doing this this way, and then how I built it.
So first of all, when you think about your approval processes in your company you might have a few very simple ones if you just have a quick document that has one or two people that have to sign off on it. But you're going to have a lot of different processes, and they're going to vary wildly as far as how complex they might get.
So you have different requirements, different levels of complexity, such as number approvers and parallel versus serial approvals, groups of people needing to approve things. So it could get a little crazy with how you need to build your logic. And sometimes some of these out-of-the-box methods that Microsoft provides are not going to cut it. And they're going to make it a lot more difficult to build those.
So that's why I've come up with this method. It's very flexible. You build the form and the approval interface all in one in your Power App. This is a Canvas App, and this is a no-code app. I'm not a developer, so I'm not going to be showing you how to deploy any code. This is just a pretty simple thing that power users, that level of people can do, power users and business users.
So I'm going to go over with you now the options that Microsoft provides and the levels. So these are the levels of complexity going down the screen as far as what's available and how simple and difficult they are. So you have, the first ones are easy, just out-of-the-box approvals that you can create. You have Microsoft's SharePoint content approval setting that exists in all lists and libraries. It's just a setting that you turn on.
You had the request sign off concept that is a flow that you can run on items in lists and libraries. And you have an easy little set a reminder, and that's a flow as well. And then you have, over in Teams, you have the ability to go to the approvals app and create an approval form. And those are all pretty easy, just a couple of clicks out-of-the-box methods. But then once your approval process requires something a little different or something more complex, those aren't going to work.
So then you have medium level complexity, and those involve the templates, like the flow templates when you go to the main flow interface, and you're presented with the ability to search through templates and pick one you like. So you could use the templates as they are. You could take one and adjust it to how you need it. But that is going to require a little bit more of technical knowledge of how to edit those flows.
And then you get to the crazy complex ones where you can just start from blank and build your process however you need it to be with many different conditions, branches, approvals, multiple products involved, like SharePoint, Power Apps, Power Automate Forms and Teams. And then that's going to be
 40:03
40:03
