[MUSIC PLAYING] Hi. My name is Alvaro Vitta. I'm a Principal Solutions Architect with Quest. Let's talk about Hybrid Active Directory security and a lifecycle methodology around it. So a continuous lifecycle methodology in security ensures that you don't have a static methodology.
Companies are not static. Things are changing, they're expanding, they're contracting all the time. Things are moving within the environment. So you want to be able to have a methodology that is continuously being implemented.
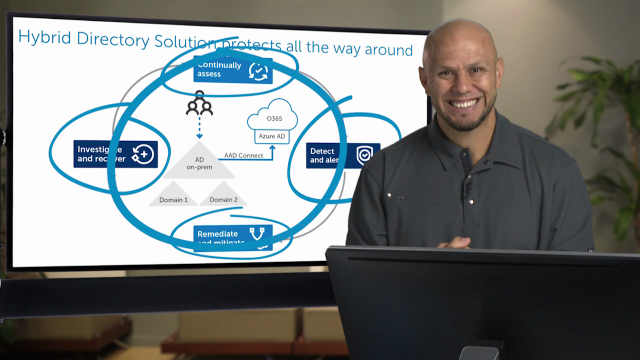
So the first thing you want to do is you want to continuously assess who has access to what. You want to be able to detect and alert what they're doing with that access and remediate any unauthorized access and mitigate it from happening again. And you want to investigate and recover from security incidents within your organization.
So continuously assess. So here what we want to do is we want to assess who has access to what sensitive data and how did they get this access? For example, who has privileged access in Active Directory, like the ability to reset passwords, the ability to backup and recover Active Directory, the ability to change sensitive groups within the organization-- not only technical privilege groups like domain admins, but maybe executive or C level security groups that may grant access to sensitive information within the organization.
Then you want to detect and alert. And detect and alert, what we want to do here, is once we establish a security baseline, we want to ensure that we alert what is changing from that original security baseline. So if I granted permissions to specific people to do things within Active Directory, I want to report when those permissions deviate, when they change over time.
So I want to know if there's any suspicious privileged accounts that have been changed within the environment. I want to know how many changes occurred that could be significant or indicative of an insider threat activity like an employee or contractor doing things that they shouldn't do. I want to know very quickly if an intrusion has happened within the organization.
And then I want to know, are we under attack right now? There's things happening that are anomalies within the organization. I want to be able to know these things.
Then I want to remediate and mitigate. So what this means is I want to be able to have self-healing or self-remediating mechanisms that are automated controls that allow me to say OK, if somebody gets added to a particular group, in order for that to happen they need to be part of an authorized list of people. Even if I have domain admin rights, I want to be able to make sure that I have that kind of control. I want to be able to have my sys admins and my administrators within the organization to have the rights to do things that they're supposed to do. Nothing more, nothing less. A need-to-know basis.
I want to make sure that my sensitive resources are protected, like things like security groups within the organization. I want to make sure that only certain people can modify these groups. And I want to also make sure that if somebody needs access to this group, there's an approval process behind it.
I want to make sure that it doesn't take me too long to remediate unauthorized resources that could compromise the integrity of my Active Directory environment. I want to be able to, whether I'm there or not, to be remediated. I want it to be automatic, I want it to be self-healing in nature.
I want to investigate and recover. I want to know when a breach happened, how it came to be, how it entered the organization, the scope of people affected, what systems and resources are affected within the organization. Once I find that, I want to be able to then recover automatically across geographies, across whether I'm remote or local.
I want to be able to do it with different people. So if somebody that is responsible for that recovery process has left the company, I want somebody else to go and simply click on a button and recover that automatically, as quickly as possible so that the organization can come back online and be productive again.
So within our organization, we provide you with something called the Active Directory security suite. This suite gives you and maps all of this lifecycle methodology. So for example, Enterprise Reporter will assist you in assessing who's got access to what and who's got permissions where.
Then Change Auditor for Active Directory will allow you to detect and alert what people are doing with that access and those permissions within Active Directory. Then we have products like ActiveRoles Server and GPOADmin that will ensure that within GPOs, for example, GPO admin will tell you these people should only have this access, and if they need more than that, they need an approval process. In Active Directory, ActiveRoles Server will do the same so that you have approval processes, so you have temporary security groups. So that you have the ability of having a least privileged access model where administrators will only have access to do what they're supposed to do-- nothing more, nothing less.
And lastly, we have the IT security search that allows you to very simply do searches across the environment to understand how a particular incident came to be, and then Recovery Manager for Active Directory, which automatically can recover whether from a partial outage or a complete outage that affects all of your domain controllers, all of your schema in Active Directory, and quickly bring that up to an operational state.
In summary, our hybrid directory solution protects you all the way around-- on-prem resources and cloud-based resources, in a hybrid Active Directory model where you're on-prem AD is being synced to the cloud. So we'll do continuously assessing of permissions, detecting and alerting, remediating and mediating
 07:05
07:05
