I'm Shawn Barker, product manager at Quest Software. And I'm going to show you how Quest On Demand Audit integrates with Specterops Bloodhound Enterprise to help you secure your Active Directory attack paths and improve your overall security posture. Traditional approaches to Active Directory security have included patch management to mitigate zero-day exploits, as well as detection and response tools to enable quick response after a breach occurs. AD administrators have also been accustomed to thinking of AD security in terms of lists of configuration settings, hardening the directory by going through a long checklist of configurations known as vulnerability management.
Patch and vulnerability management are important in reducing the attack surface adversaries can leverage to breach AD. However, both disciplines look at misconfigurations in isolation and not in context of how and how likely an adversary could use them to get from an ordinary compromised user account to your organization's most valuable assets. Protecting your most critical assets is one of the main goals of AD security. Because if an adversary gains control of any of these assets, they can get to whatever their objective is. These critical assets are usually referred to as the control plane or Tier 0.
In most environments, there are many, many paths from ordinary user accounts that could be compromised to your Tier 0 objects. Vulnerability management remediates discrete configurations that need to be hardened. But looks at these settings in isolation and not in the context of the attack paths available to an adversary. Patching vulnerabilities can be like playing a game of whac-a-mole. As soon as you fix one, another one pops up. An adversary only needs one path. And there are usually thousands available.
An easy way to visualize AD attack paths is like a road map of the United States. The adversary is in San Francisco. And your valuables are on the island of Manhattan. There are literally millions of ways the adversary can get from where they are to the target. You can shut down one highway along the way. But there will be hundreds of ways around that highway.
This is what a simple AD attack path looks like. It starts when an ordinary, unprivileged user account is compromised by a phishing scheme. Mitch is a member of the Helpdesk group. Because of security group delegation, members of a group get all the privileges that come with that group. So any permission held by Helpdesk group is now granted to Mitch. The Helpdesk group also belongs to another group called Tier 2 Support.
Group nesting is very common and can give a lot of unintended privilege to our ordinary Mitch user so that he's suddenly overprivileged. The Tier 2 support group grants local administrator rights over the payment Payment-01 machine. The Payment-01 server has a log on session from a privileged service account. It's trivial for an adversary to abuse that using the Windows token model and harvest those credentials. When the adversary gains access to the Auston-ADM service account, they have the Add Member privilege over the domain admins group. And they can add themselves.
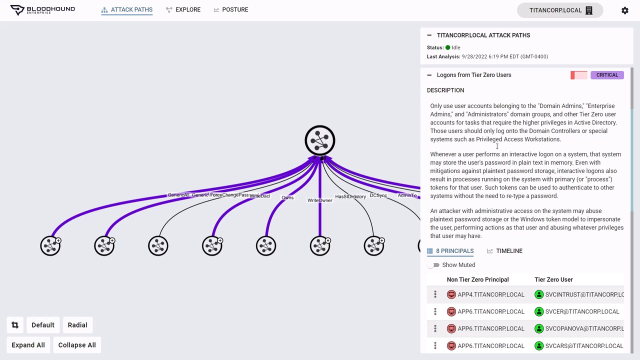
The adversary has completed the AD attack path from an ordinary user to Tier 0 and gains control over AD in a few steps. Bloodhound Enterprise makes identifying all add attack paths in your environment possible. At the top of the graph are your most valuable resources. Bloodhound Enterprise automatically defines Tier 0 assets in this node by including domain controllers, privileged accounts, well-known admin groups, domain-level GPOs, and any principals that have control over these objects.
And you can add additional assets to Tier 0, as appropriate, such as the Azure AD connect server, [? M cell ?] account certificate servers, and your AD backup host. Bloodhound Enterprise uses graph theory to calculate and visually identify all attack paths from ordinary user accounts to your Tier 0 assets. Since most environments will have thousands, even millions of attack paths, Bloodhound Enterprise focuses on these choke points at the top, the last step in an attack path to your Tier 0 assets.
If you can remediate the choke point, you are eliminating the hundreds or thousands of paths below that point. So if an attacker were to compromise one of the accounts underneath and elevate their privileges, they will be prevented from accessing your Tier 0 assets. Removing a choke point is akin to closing a bridge to Manhattan, preventing the adversary from traveling that last leg to their target. Bloodhound Enterprise further prioritizes these choke points to help you focus on the ones that will most drastically reduce your exposure and improve your AD security posture.
On the right, are all the choke point vulnerabilities that can be exploited if I select one of the critical choke points, Kerberos delegation on Tier 0 objects, Bloodhound identifies the accounts that are exposed. The product indicates the exposure. This vulnerability has in the environment specifically what percentage of principles can be used to exploit it. Bloodhound also provides practical step-by-step guidance on how to remediate this vulnerability and eliminate the attack path.
Quest On Demand Audit integrates with Bloodhound Enterprise to automatically monitor all Tier 0 objects for any sign of compromise. When any suspicious activity associated with Tier 0 assets occurs, On Demand Audit surfaces that activity and the security dashboard.
Dozens of built-in searches monitor your Tier 0 GPOs, servers, users, and groups across AD and Azure for activity which could indicate an incursion or compromise of your Tier 0 and to alert you proactively when suspicious activity is detected. Given the many application and permission dependencies in AD, the unfortunate reality is that attack path choke points will take investigation and time, often months or longer, to remediate.
To ensure the security of your Tier 0 assets, On Demand Audit can also monitor these exposed choke points for active threats so you can ensure they are not being exploited while you work to remove them. For example, Bloodhound Enterprise
 07:30
07:30
