This is a short video to demonstrate the powerful forensic capabilities of IT Security Search. My name is Shawny Reiner and I'm a strategic solutions consultant for Quest Software. IT Security Search is a web based interface and console for several of our management and security solutions. It's free with any of the five solutions it works with and it can be used with one, or all five of the solutions, which are Change Auditor, Enterprise Reporter, InTrust, Active Roles, and Recovery Manager for Active Directory.
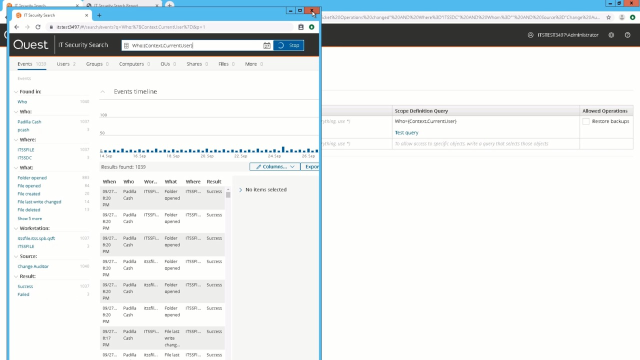
IT Security Search uses the data from these products to provide quick consolidated and correlated forensic searches of changes, issues, and general information in your environment. As you can see, ITSS looks very much like an internet search engine. And it pretty much works like that, but it's searching across the data of the solutions I mentioned before.
GPO changes can be very problematic, invasive, and extremely difficult to pinpoint. But with IT Security Search, it's pretty easy to discover what changed and that's what I'm going to demonstrate. So let's assume, in this scenario, users are reporting that their favorites bar and i.e. has changed or they're having some kind of issue with it. The suspicion is that it's a GPO change. But I have no idea what GPO, or even maybe what GPO setting, has changed. So I need to find it quickly.
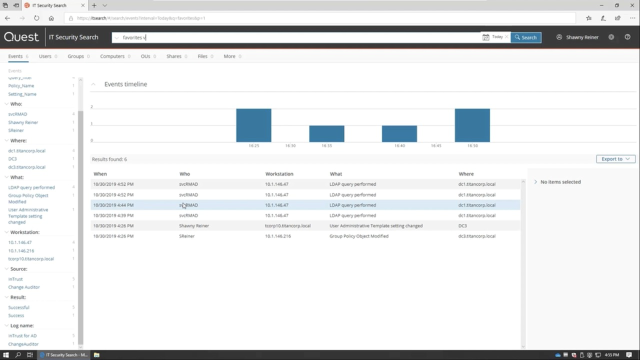
So I'm going to type in this IT Security Search field the information that I do know. And I know it's related to their favorites. So that's what I'm going to start with. So I'm just going to simply type the word favorites. And since I know that this problem just started, I'm going to filter it by date. I'm going to do today. I could do any one-- any of these or I could do a custom search.
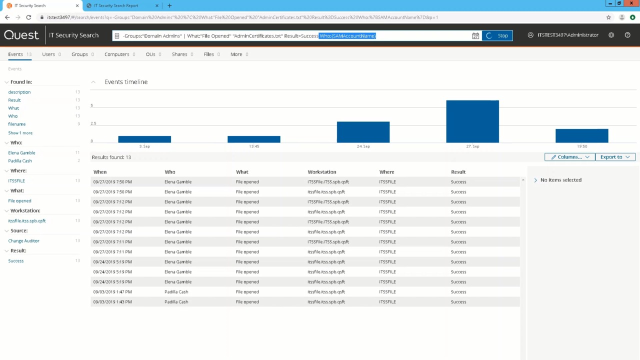
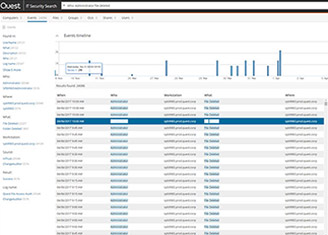
Because I was able to do a fairly narrow search, it found the events I was looking for pretty quickly. But as it does begin to search, if you've had to do a broader search, it will organize this information, as you can see, by who, where, what. The workstation, the source, the result of the change, and all of these are clickable links to help you begin to further narrow that search and hone in on the events you're looking for. But since it was able to find these pretty quickly, and I'm looking for a GPO change, I'm going to take a look at these two events that came up because they're related to GPO changes today.
And if I click on them, then over here in this area, you get a brief description of the details. And as you can see, it's giving me all of the information. It's telling me what part of the GPO changed. That before this particular setting was not configured and now it's enabled. And then it gives me a description, template turned off, favorites bar, setting changed. And this is the name of the GPO right here. And it even tells me who changed it. In this case, it was me.
Also, I can click on the other link because that one was from Change Auditor. This one's InTrust, which gives me another look at the actual logged event-- windows event log. And this one, again, tells me the name of the GPO and the setting that was changed, yield value. And I can take a look at the details of these to get even further information by simply clicking View Details.
This gives you a nice view of every part of the change that Change Auditor captured. If we had clicked on the InTrust one it would be the same, what InTrust captured. And now we know exactly what changed and what we need to go back and fix so that the issue is resolved. So this is just one way that ITSS with the data from our management security and auditing solutions can provide powerful forensic searching to understand and know your environment.
 04:05
04:05